Lexhunt
Lexhunt is an artifact processing and digital investigation tool. In the course of responding to digital security incidents, forensic analysts handle evidence from diverse sources, including disk copies, data collected from various tools, system and network logs, and more. LexHunt empowers CSIRT LEXFO analysts to swiftly, effectively, and consistently process all these artifacts. Its primary aim is to facilitate digital investigations by enabling the tracing of attackers' modus operandi, from the initial attack to its eventual detection, over a historical timeline.
+220
Artifact types supported
38
Data enrichment filters
150
Visualization elements
Approach
Maximum Compatibility
- Native Disk Copy and Log Management: LexHunt supports bit-by-bit disk copies and flat file logs, ensuring seamless compatibility with various data sources
- DFIR-ORC Integration: LexHunt seamlessly integrates with DFIR-ORC collections, allowing for comprehensive data handling
- Cross-Platform Compatibility: It is compatible with both Windows and Linux trace processing, catering to a wide range of systems
Automation and Speed
- Automation features and quick timeline construction based on available artifacts
- Using six artifact filters to expedite processing and provide analysts with preliminary timelines swiftly
- A Python 3 tool developed(*) in house, for and by CSIRT Lexfo analysts
- (*) LexHunt relies on other Open Source tools in addition to custom solutions developed by CSIRT Lexfo
Data Enrichment
- Traces are enriched with metadata, categorizing data by source and type
- LexHunt implements 38 customized filters, comprising over 9100 lines of code, informed by CSIRT LEXFO's expertise
- Supports over 220 data types for trace enrichment, ensuring thorough analysis
- Event descriptions are standardized in English, enhancing readability of investigation reports
Optimized Investigations
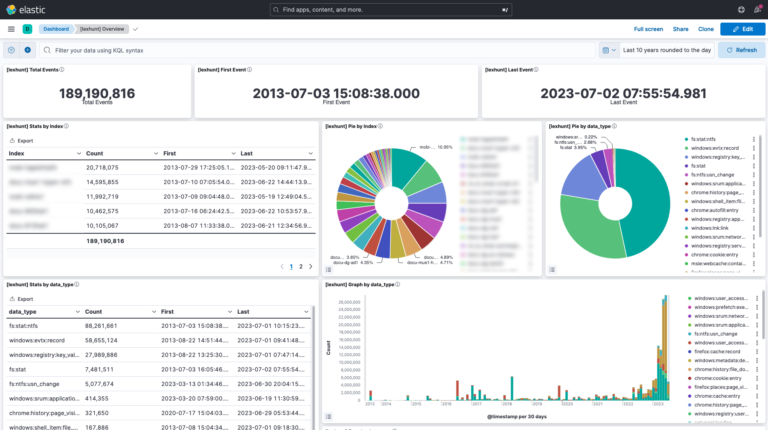
- LexHunt employs the ELK(*) stack for evidence import, storage, and analysis
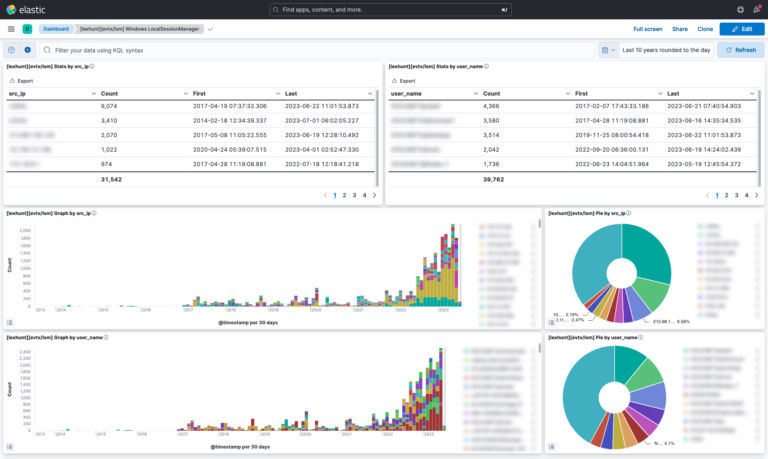
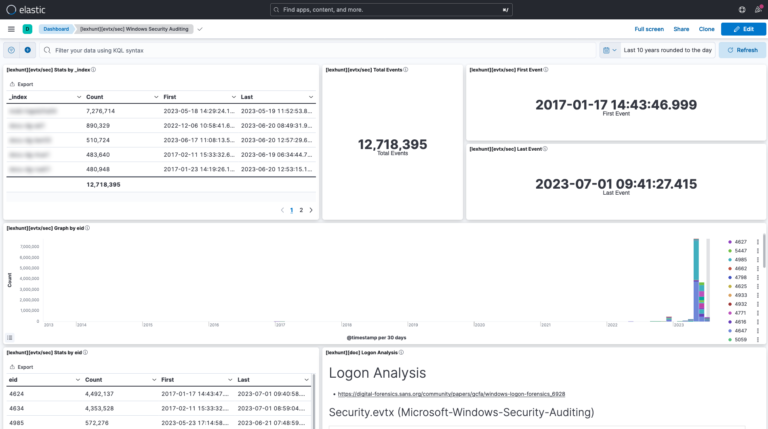
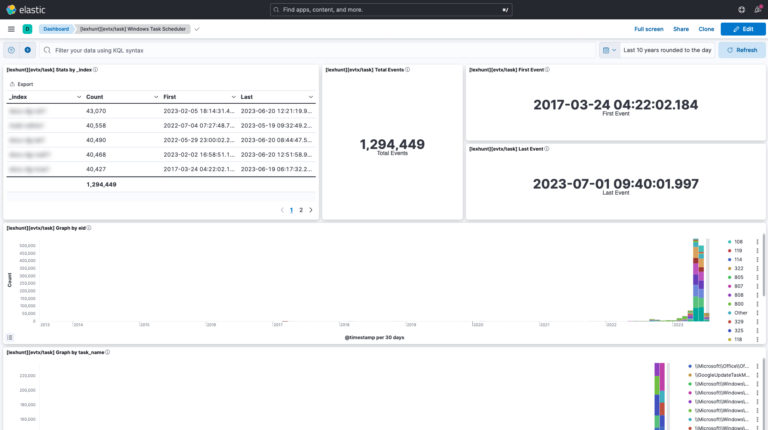
- Over 10 dashboards and 150 visualization elements to expedite investigations
- Internal procedures enable CSIRT LEXFO analysts to quickly isolate initial investigation results
- (*) ELK stack stands for Elasticsearch, Logstash, and Kibana, which are widely used tools for log and data analysis
Technology Platforms